Mitigating Transitive Vulnerabilities in Application Security
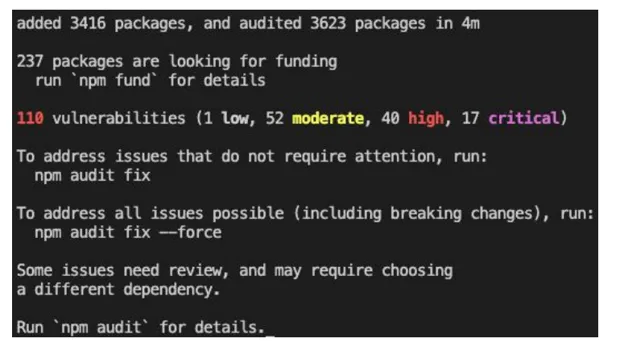
Understanding Transitive Vulnerabilities
Transitive vulnerabilities are becoming a significant concern in the realm of application security. These vulnerabilities can arise from third-party dependencies that introduce risks into an organization's applications.
Risks and Mitigation Strategies
- Identify Potential Threats: Organizations should regularly assess their software for known vulnerabilities.
- Automate Security Processes: Automation can significantly reduce the risk of human error in security practices.
- Educate Teams: Continuous training for development and security teams is essential to stay ahead of evolving threats.
Conclusion
As the landscape of application security evolves, understanding and mitigating the risks associated with transitive vulnerabilities becomes increasingly important. By implementing automated solutions and maintaining vigilance, organizations can better protect themselves against potential threats.
This article was prepared using information from open sources in accordance with the principles of Ethical Policy. The editorial team is not responsible for absolute accuracy, as it relies on data from the sources referenced.