Security Threats and Privacy Concerns in Telecoms During Conflicts
Understanding Security Threats in Telecoms
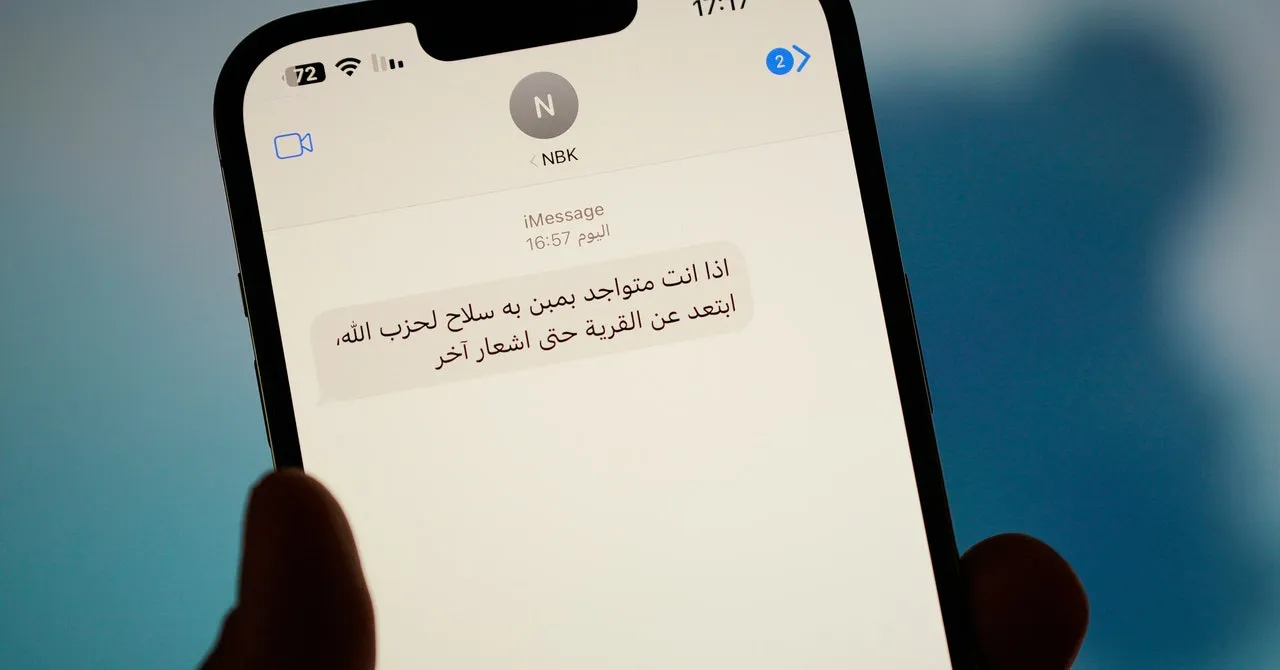
The current geopolitical climate has led to a surge in security threats affecting communication technologies. With ongoing conflicts in regions like the Middle East, the potential for privacy breaches and hacking incidents has increased dramatically. For instance, following escalating tensions, Lebanese civilians received alarming SMS messages purportedly warning them of strikes and attacks, stirring panic.
The Role of Hacking in Modern Conflicts
Hacking has evolved into a tool of warfare, affecting both sides of the conflict. As seen recently, Lebanese recipients received an SMS with a threat disguised under a masked sender. Such actions highlight a significant erosion of privacy, forcing individuals to reconsider the security of their communication channels.
Consequences of Insecure Communication
- Increased anxiety among civilians
- Panic induced by ambiguous warnings
- Potential loss of personal and sensitive information
Call for Enhanced Security Measures
To combat the rising hacking threats and privacy infringements, telecom companies must invest in now mechanisms that will better safeguard user data. Ensuring transparency and trust in communication channels is essential to maintain user confidence amid such crises.
This article was prepared using information from open sources in accordance with the principles of Ethical Policy. The editorial team is not responsible for absolute accuracy, as it relies on data from the sources referenced.